I have been dorking with IDSs since the late 1990ies, and really got involved with SNORT when I used it to corroborate the data for the IDS I built for my Master's Thesis. Anyway, IDSs have never really been easy to set up and monitor.
So what I use at home most often is the bootable Knoppix type. This avoids the problems of setup, which can be a HUGE pain. For instance, to get Sguil, one of my favorite GUIs for Snort, to run, you'll need to get Sguil, Libpcap, Libnet, Snort, P0f, tcpflow, and maybe a few other things to work together. I have tried on a couple of occasions to get this to work, and gave up because of all the dependencies required, which I could never get to flush out.
I have gotten BASE to work as a GUI into Snort, and it is OK, but I gotta say that I really like Sguil, and wanted that, especially after reading The TAO of Network Security Monitoring. That is when I found the Sguil Knoppix CD. When typing this blog, I noticed that my old iso CD (ver 1.0) has been superseded by the securix-nsm.
I have yet to try the new Securix NSM, so if anyone beats me to the punch, leave me a post.
Since they no longer post their instructions for the old Squil Security Monitor CD, here is the quick instructions. This will not allow you to tailor anything, but it will get you started fast. Note, these are the instructions for the OLDER Iso, because that is what I'm using.
boot with
#linux ip=10.10.10.10 systemtype=console hostname=whatever
#/etc/init.d/mysql start
#/etc/init.d/ntop.default start
#/etc/init.d/apache2 start
#/etc/init.d/sguild start
#sensor default start
#sguilc
This will bring up a dialog box:
Sguildhost: localhost
Sguild port: 7734
username: sguil
password: password
to view with BASE: right-click for menu, select Firefox (ignore the errors)
userid: admin
password: password
to view NTOP results: click on NTOP bookmark
That is it. Here are the FULL quick instructions, which I've pulled from the wayback machine:

So what I use at home most often is the bootable Knoppix type. This avoids the problems of setup, which can be a HUGE pain. For instance, to get Sguil, one of my favorite GUIs for Snort, to run, you'll need to get Sguil, Libpcap, Libnet, Snort, P0f, tcpflow, and maybe a few other things to work together. I have tried on a couple of occasions to get this to work, and gave up because of all the dependencies required, which I could never get to flush out.
I have gotten BASE to work as a GUI into Snort, and it is OK, but I gotta say that I really like Sguil, and wanted that, especially after reading The TAO of Network Security Monitoring. That is when I found the Sguil Knoppix CD. When typing this blog, I noticed that my old iso CD (ver 1.0) has been superseded by the securix-nsm.
I have yet to try the new Securix NSM, so if anyone beats me to the punch, leave me a post.
Since they no longer post their instructions for the old Squil Security Monitor CD, here is the quick instructions. This will not allow you to tailor anything, but it will get you started fast. Note, these are the instructions for the OLDER Iso, because that is what I'm using.
boot with
#linux ip=10.10.10.10 systemtype=console hostname=whatever
#/etc/init.d/mysql start
#/etc/init.d/ntop.default start
#/etc/init.d/apache2 start
#/etc/init.d/sguild start
#sensor default start
#sguilc
This will bring up a dialog box:
Sguildhost: localhost
Sguild port: 7734
username: sguil
password: password
to view with BASE: right-click for menu, select Firefox (ignore the errors)
userid: admin
password: password
to view NTOP results: click on NTOP bookmark
That is it. Here are the FULL quick instructions, which I've pulled from the wayback machine:
a. ALL-IN-ONE
For people new to knoppix-nsm this is the best place to start. Here you can be up in and running in minutes with a complete server/sensor/console environment.
Note: If you run this in a noisy network environment you will fill up your RAM/swap very qucikly.
Step 1 - Boot
When you are greeted with the boot screen you have two options:
- Hit enter and boot with the system defaults, or
boot> - you can customise the ip address (Class C network address automatically set), system type (systemtype) and hostname when booting to the live CD,
boot> linux ip=192.168.77.1 systemtype=console hostname=securix
The default settings:
- systemtype: sersen (server/sensor) this is used to define default firewall policies
- IP: 192.168.100.1.
- network: 192.168.100.0
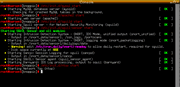
Step 2 - Start System Processes
Note: Before you proceed with the following instructions ensure you have the network configured for your environemnt, by default you will only be able to access resouces on the 192.168.100.0 network. The default firewall on a sersen will be blocking all new outbound connections except icmp. See Netwok Setup quick guide if you want to make changes, for more details on the firewall see the firewallsection in architecture page for more details on the default policies.
Successfully booted?
You should now be looking a the default fluxbox environment. By defalt the all-in-one server/sensor configuration will log output to both the snort db (for BASE) and sguild db and monitor on eth0.
- Open a root console (right click for menu),
- Start MySQL,
# /etc/init.d/mysql start - Start Apache web server,
# /etc/init.d/apache2 start - Start the Sguil server,
# /etc/init.d/sguild start - Start the Sguil-sensor, the following script will start all the processes required for a sensor, in the right sequence. If you want to start individual processes manually see the Architecture page for details on which scripts to use and the best sequence to start them in to minimise problems.
# sensor default start - Start ntop, Caution: Live CD - by default the previous step will not start ntop on the live CD. Starting ntop with everything else already running may cause the system to slow to a stand still. The following will start ntop, if you experince system slow down and want to test ntop stop the sensor first.
# /etc/init.d/ntop start
If all went well you should have seen the following results.

Step 3 - Start Sguil client
Now we want to start looking at events.
- Open a console (non-root) and enter
# sguilc - or right click menu ->NSM->Sguil Cllent
- Log in with the following details, (take note of ssl option, all connections are ssl encrypted)
host: localhost (defualt) port: 7734 (default) username: sguil password: password OpenSSL: selected (default)

You should now be looking at the sguil console and ready to start your journey into the world of NSM and sguil.
Step 4 - Start BASE client
By default, knoppix-nsm also logs data for viewing with BASE, aka snort compitable database. Although this is not recommeded as it can slow snort down by having to log two different types of output, it is great for demonstration purposes.
- Start firefox (right click for menu, uder NSM submenu),
- click the base option on the bookmark toolbar or enter the following url, (take note of https, all web connections are ssl encrypted)
localhost/base/ - Login in,
username: admin
password: password

You can now begin to navigate around and view events with base.
Step 5 - View Statistical data with Ntop
Ntop is busy collecting network statistical data for us that can be used to help identify network normalcy patterns and anomalous activities. Ntop gives us a little bit more to help in the identification of false positives.
- click the ntop option in the bookmark toolbar or enter the following url, (take note of https, even ntop is configured with ssl)
localhost:3000/
Step 6 - Test it
To test everything works you will need to generete an alert, this is easy to do as all the snort alerts are enabled by defaults so a ping will do. You can do this in one of two ways:
- Ping from this box to another host on the network, assuming you have the network configured properly, or
- Ping between two hosts on the segment you are monitoring (assumes you are not on a switch, no point being there anyway as you will only see broadcast traffic).
If you were able to send out/receive pings then you should neow see alerts in the sguil and BASE console along with traffic in ntop.
Comments
Post a Comment